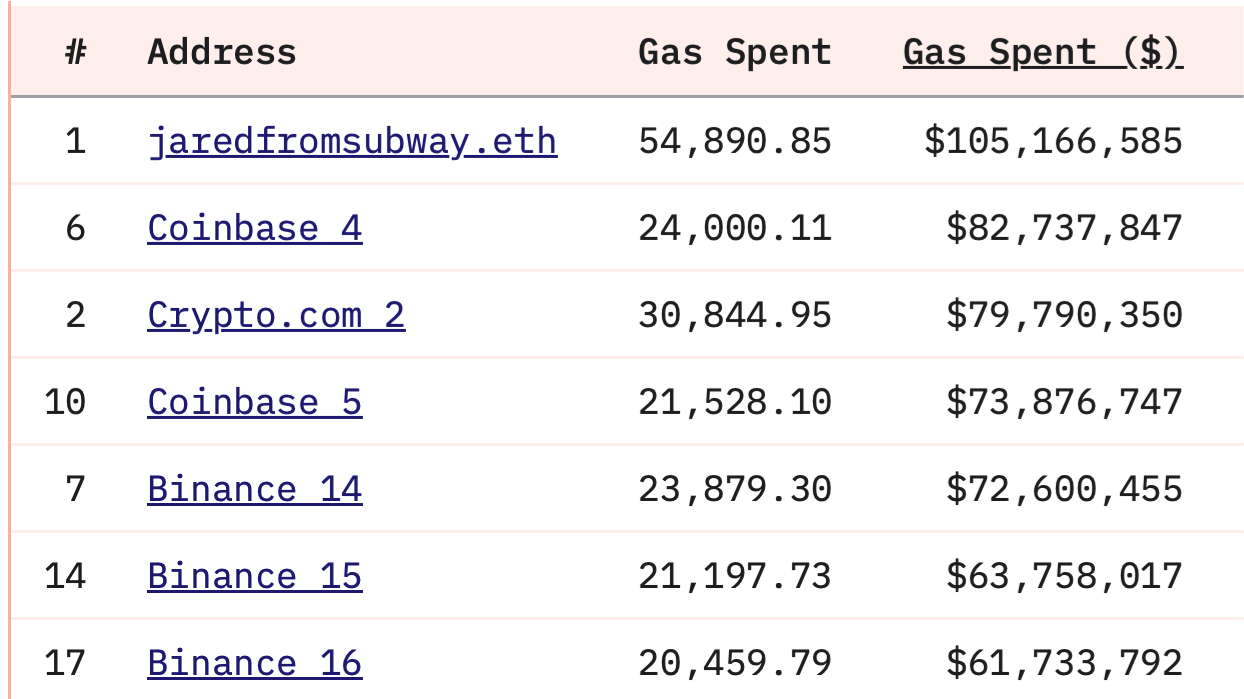
Sandwich attacks are a ubiquitous facet of DeFi life, even inspiring meme sandwich bot accounts such as jaredfromsubway.eth.
The impact of sandwich attacks is significant. To give you an idea of the scope of the issue, the largest gas spender of all time is currently the jaredfromsubway account — with more than $100 million worth of gas spent.
If this one account has spent $100 million on gas, how much are they making, and more to the point how much are they and other attackers stealing from users who are simply trying to swap tokens on decentralized exchanges?
A Simple Swap Recipe
Swapping tokens seems like a simple process. A user has some amount of token X and they want to swap it for token Y using an Automated Market Maker (AMM) like the kind pioneered by Uniswap. There is however a vulnerability in this process — the liquidity reserves used by the AMM can be manipulated to steal tokens from the user.
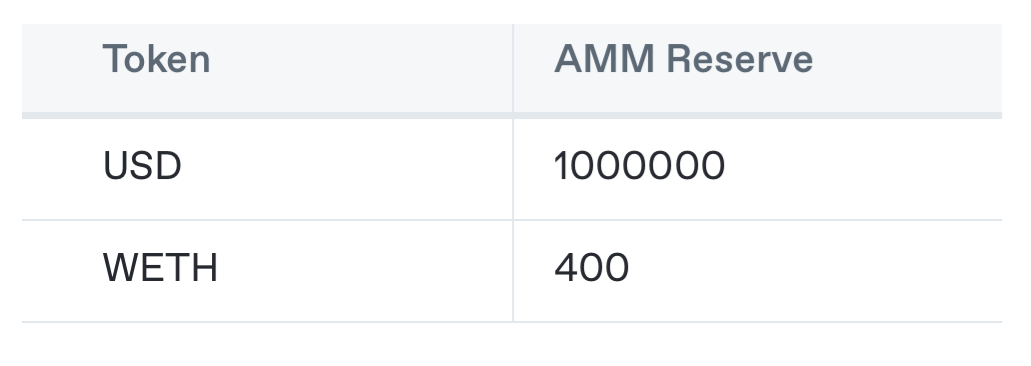
Here’s an example. Say a user wants to swap 5000 USD for WETH. They will use the following liquidity pool which currently has $2 million in liquidity and a WETH price of $2500.
Using this pool the user swaps 5000 USD for 1.99 WETH - which has a market value of $4975.
How Sandwich Attacks Are Made
Swaps like the above don’t exist in a vacuum and predatory bots are often waiting to take advantage of DEX mechanics. In this example, the user will place a swap again, but this time jaredfromsubway or some other sandwich maker will step in.
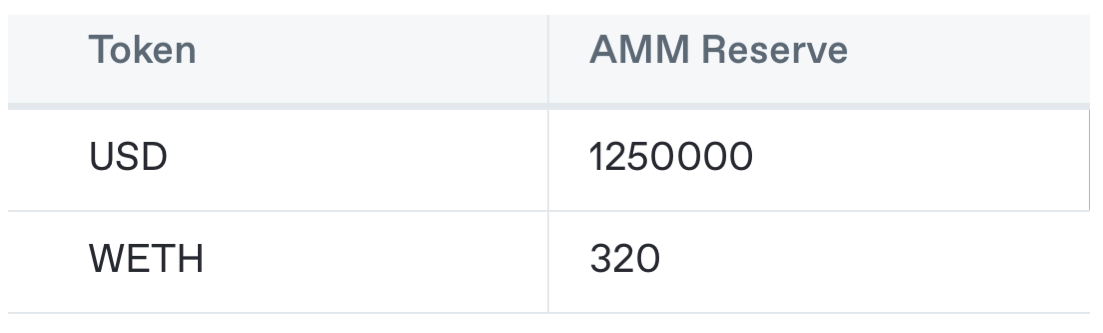
First, the attacker places a swap at a higher gas price than the original user swap — causing their attack to be executed first in the blockchain. Their goal is to make WETH very expensive for the unsuspecting user. So they swap 250k USD for 80 WETH.
The price of WETH is now $3906. That is expensive! Why would the user buy at that price? Well, they’ve already submitted their transaction to the blockchain. The attacker has “frontrun” the user and now the user has no option to back out if they have specified the wrong maximum slippage.
So, now the user only gets 1.28 WETH for their original 5000 USD — for a market value of $3200. They’ve had nearly $1800 stolen from them.
To complete the sandwich, the attacker sells back the 80 WETH they obtained from the initial attack and pockets the ill-gotten gains.
The Balancing Act
The Automatic Atomic Arbitrage pioneered in Salty.IO and Zero DEX performs arbitrage across multiple pools during a user’s swap transaction. Typically this kind of arbitrage is done by external bots, but with AAA it is done by the exchange itself. The profits normally extracted by arbitrage bots are distributed to the liquidity providers and stakers — encouraging deeper liquidity and allowing for zero fees on all swaps.
Let’s revisit the user swapping 5000 USD for WETH. As in the first example the user obtains 1.99 WETH with a market value of $4975.
Then, within the same transaction, the following arbitrage trade is placed across three pools: WETH->USD->WBTC->WETH. The effect of this arbitrage trade is to “undo” some of the impact from the user’s WETH purchase and bring the WETH price into balance with the other pools.
How does this mechanic affect sandwich attacks? Let’s see!
The Inedible Sandwich
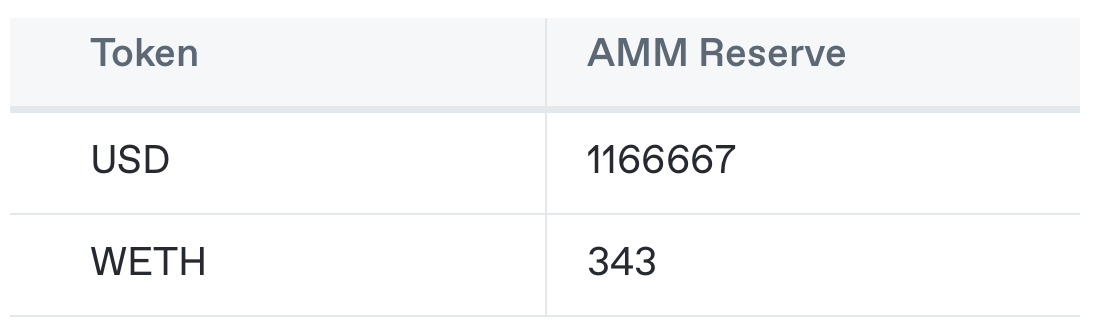
The attacker sees that the user is about to swap 5000 USD for WETH — and again tries to make WETH expensive for the user by swapping 250k USD for WETH. The attacker obtains 80 WETH like they did before, but this time something happens. Within the attacker’s initial swap, automatic arbitrage is performed and now the reserves look like this (assuming roughly $2 million liquidity in each of the three involved pools).
With arbitrage the WETH price after attacker’s initial swap and automatic arbitrage is now $3401. Still not great for the user, but what about the attacker? The attacker still has their 80 WETH from their initial swap. Now if they sell that 80 WETH back they only have 220k USD. So because of arbitrage the attacker effectively loses $30k on this sandwich attack — an effective deterrent.
It turns out that in this example the best option for the attacker would be to start their attack with an initial swap of 5000 USD for WETH — and then pocket a sandwich attack profit of $16. So, without AAA the attacker could make $1800. With AAA the attacker can make $16. Assuming gas costs are at least $8 then even this becomes completely unprofitable. An inedible sandwich.
Conclusion
The Automatic Atomic Arbitrage (AAA) pioneered within Salty.IO and Zero DEX stands as an effective deterrent against sandwich attacks, transforming what could be a potential exploit into a powerful defense mechanism.
Both platforms’ commitment to decentralization, alongside comprehensive audits by renowned firms like Trail of Bits, ABDK, and Code4rena, underscores their ambition to emerge as pioneering forces within the DeFi landscape.
For more information, please see the following official links:
Salty.IO (Ethereum)
• https://salty.io
• Twitter
• Documentation
• Discord
Zero DEX (Scroll)
• https://zerodex.org
• Twitter
• Documentation
• Discord
Disclaimer: This article is for informational purposes only and is not intended as investment advice. Please conduct careful due diligence and consult a financial advisor when considering any investment.





Great idea
Excellent